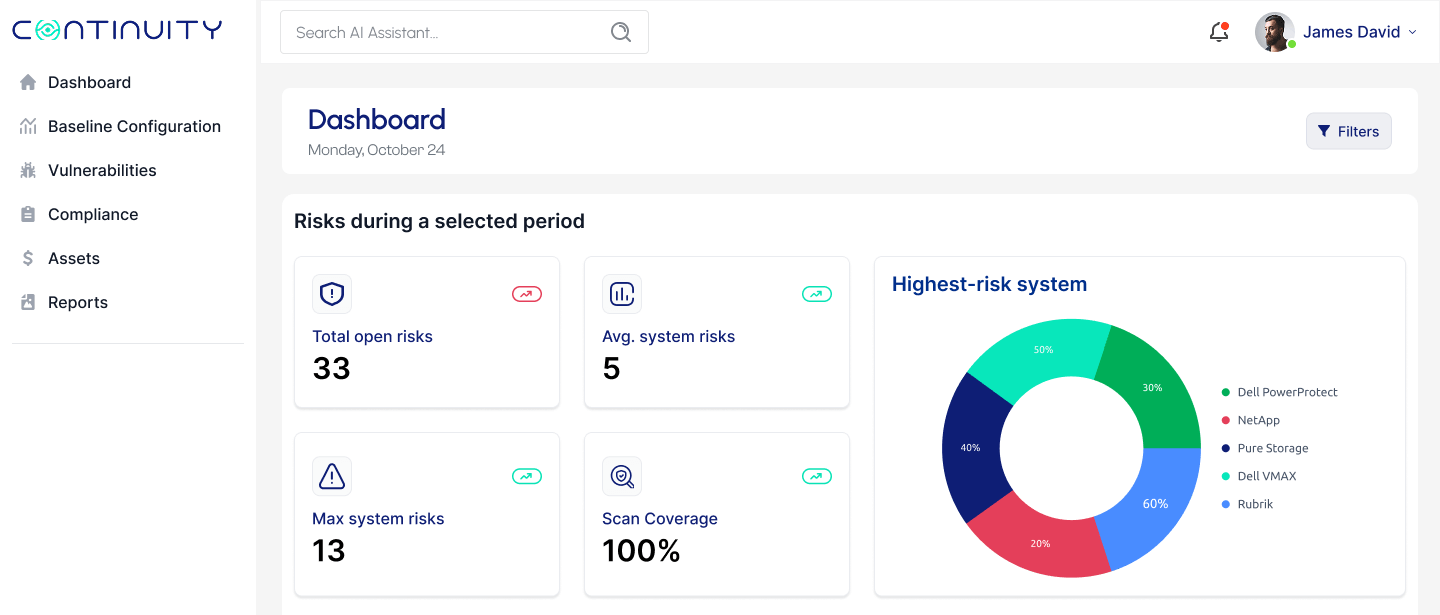
Using An Agentless Scan, StorageGuard Gives You Complete Security Oversight Of Your Storage And Backup Environment
| Access Control Lists (System) | |
| Authenticated System Communication (Zero Trust) | |
| Access Control Lists (Shares) | |
| Account Lockout | |
| Backup Isolation Principles | |
| Multi-Factor Authentication | |
| Default passwords | |
| Data at-rest Encryption | |
| End of Support Software / Firmware / OS | |
| High-Severity Security Advisories | |
| Hardened Management System (CLI, Web) |
| Immutable Backup Copy | |
| Internal Communication Encryption | |
| Logging | |
| Password Rules | |
| SAN Network Security Best Practices | |
| SSL Certificates | |
| Strong cryptography | |
| Session Restrictions | |
| #StopRansomware CISA Guidelines | |
| Users and RBAC | |
| Unused Services / Protocols are Disabled (Least Functionality) |