Dual Authorization in Storage and Backup Systems: A Technical Guide
About Continuity™
StorageGuard - by Continuity™ - is the ONLY Security Posture Management solution for Storage & Backups, helping to ensure these systems are securely configured, and compliant with industry & security standards.
In the world of information security, dual authorization (also known as the two-person rule, four-eyes principle, or dual control) is a powerful concept designed to enhance security by requiring the involvement of two individuals to approve and execute critical actions.
Unlike dual-factor authentication (2FA), which verifies a single user’s identity using multiple factors, dual authorization ensures that no single individual can perform sensitive operations alone – such as data deletion, immutability or backup changes.
In the military, the concept is designed to prevent accidental or malicious launch of nuclear weapons by a single individual. It requires two officers to simultaneously turn their keys to proceed. This collaborative safeguard also mitigates the risk of cyber threats and accidental misconfigurations, particularly in high-stakes environments like storage and backup platforms.
Why Implement Dual Authorization
The benefits of dual authorization go beyond reducing the risk of unauthorized access. This approach:
- Protects Against Data Deletion or Corruption: Dual authorization makes it significantly harder for bad actors to delete or corrupt primary or backup data. Attackers would need to compromise two separate user accounts with sufficient privileges, adding a critical layer of protection against malicious or accidental actions.
- Prevents Insider Threats: By requiring two individuals to authorize sensitive actions, it minimizes the chance of a rogue insider abusing their privileges.
- Supports Compliance: Dual authorization aligns with industry guidelines and regulatory requirements, such as NIST SP 800-53 AC-5(4): Dual Authorization, NIST SP 800-53 CP-9(7) Dual Authorization, CSA Cloud Control Matrix 04 and Swift Customer Security Controls Framework 5.1 Logical Access Control.
- Defends Against Sophisticated Cyberattacks: In the event of advanced cyberattacks, including nation-state-sponsored breaches or perimeter-breaching malware, dual authorization acts as an additional safeguard to prevent unauthorized access to sensitive systems and data, even when initial defenses are compromised.
- Hardens Your Cyber Recovery Systems: Dual authorization ensures the security and integrity of storage and backup platforms – the critical “Plan B” systems you rely on for cyber recovery. By safeguarding these systems, organizations can trust their recovery environment is uncompromised during an incident.
- Enhances Accountability: The dual approval process ensures that multiple parties are aware of and responsible for critical changes.
- Reduces Errors: Collaborative validation reduces the likelihood of costly mistakes or misconfigurations.

Implementing Dual Authorization in Storage and Backup Systems
Implementing dual authorization in storage and backup environments requires platform-specific configurations. Here’s how to set it up across several leading technologies:
| Technology | Implementing Dual Authorization |
|---|---|
| Dell PowerProtect DD (Data Domain) |
1 # Configure a Security Officer account using the following command: 2 user add socuser role security 3 # Configure an authorization policy 4 authorization policy set security-officer enabled Refer to Dell documentation for additional details. |
| IBM Storage Protect (formerly TSM) |
1 Designate one or more approval administrators by using the UPDATE ADMIN or REGISTER ADMIN commands. 2 update admin admin1 cmdapprover=yes # for new admins register admin admin2 cmdapprover=yes # List who is defined as a command approver (review command approver field) query admin * f=d 3 Enable the command approval feature 4 set commandapproval on Refer to IBM documentation for additional details. |
| Commvault | 1. To enable the Multi-Person Authorization feature, download, import, and deploy various authorization workflows from the Commvault Store. 2. Download and deploy the Get and Process Authorization workflow. 3. Download and deploy additional authorization workflows. 4. From the CommCell Browser, go to Workflows. 5. Right-click the Get and Process Authorization workflow, and then click Properties . 6. Configure the following properties: – Users who can authenticate the request: The selected users can authenticate requests. – User groups which can authenticate the request: The users of the selected user groups can authenticate requests. – Number of approvers: Number of users to authorize the request. – Default approvers user group: The users of the selected user group can authenticate or authorize requests from the preceding Business Logic workflows. The default value is Master user group. If no user and user group is specified in any of the configuration properties, then the users of master group are considered as approvers (for Get and Process authorization workflow). Authorization workflow examples 1. Delete Backup Set Authorization 2. Client Properties Modification Authorization 3. Delete Company Authorization 4. Delete Jobs Authorization 5. Enable Root Access Authorization 6. Delete Plan Authorization 7. Delete Company Authorization 8. Delete Subclient Authorization 9. Delete Storage Policy Authorization 10. Delete Storage Policy Copy Authorization 11. Delete SQL Database Authorization 12. Modify Active Job Authorization 13. Disable Compliance Lock And more. Refer to Commvault documentation for additional details. |
| NetApp ONTAP | 1 Check that the Mail From and Mail Server parameters are configured: 2 event config show 3 If not, configure them using the following command: event config modify -mail-from email_address -mail-server server_name 4 Create the MAV approval group: 5 security multi-admin-verify approval-group create [ -vserver svm_name] -name group_name -approvers approver1[,approver2…] [[-email address1], address1…] where: vserver – Only the admin SVM is supported in this release. name – The MAV group name, up to 64 characters. approvers – The list of one or more approvers. email – One or more email addresses that are notified when a request is created, approved, vetoed, or executed. 6 Verify group creation and membership: 7 security multi-admin-verify approval-group show 8 Enable MAV functionality 9 security multi-admin-verify modify -approval-groups group1[,group2…] [-required-approvers nn ] -enabled true [ -execution-expiry [nnh][nnm][nns]] [ -approval-expiry [nnh][nnm][nns]] 10 create multi-admin verification (MAV) rules to designate operations requiring approval 11 security multi-admin-verify rule create -operation “protected_operation” [-query operation_subset] [parameters] example: security multi-admin-verify rule create -operation “volume delete” -query “-vserver vs0” 12 Consider also enabling Dynamic authorization. Dynamic authorization uses a trust scoring system to assign users a different level of trust depending on the authorization policies. Based on the user’s trust level, an activity they perform can be allowed or denied, or the user can be prompted for further authentication. Refer to NetApp documentation for additional detail. |
These procedures not only bolster security but also provide a framework for operational integrity and compliance across diverse storage and backup platforms.
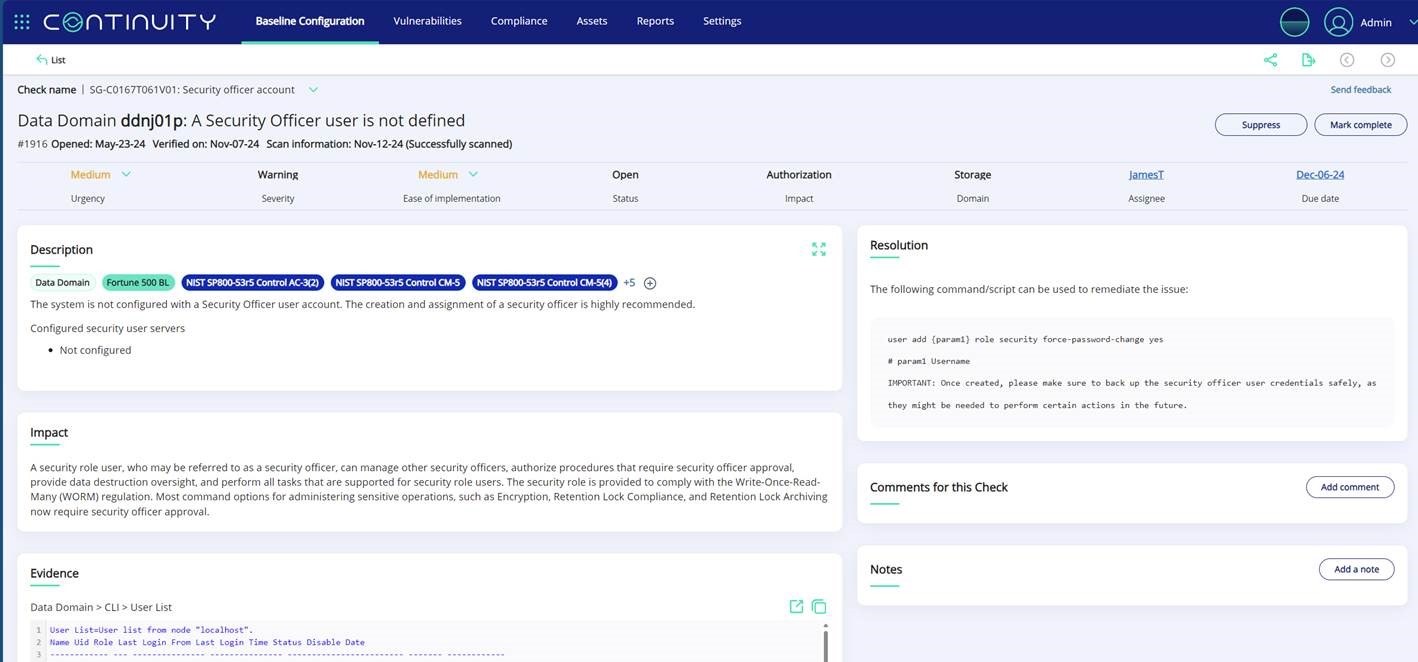
How StorageGuard Simplifies Dual Authorization Auditing
While dual authorization is a critical security feature, ensuring its consistent and correct configuration across multiple storage and backup platforms can be challenging. This is where StorageGuard comes in. StorageGuard provides a unified framework to audit and validate the correct implementation of security controls at scale including dual authorization, offering:
- Automated Configuration Audits: Verify dual authorization settings on Dell, IBM, Commvault, NetApp and more.
- Cross-Platform Consistency: Detect discrepancies and misconfigurations across different environments.
- Compliance Reporting: Generate detailed reports to demonstrate compliance with regulatory standards.
- Ease of Use: Streamline security governance by providing a single pane of glass for monitoring and managing dual authorization across all supported platforms.
With StorageGuard, organizations can ensure that their storage and backup systems are configured with the highest levels of security, reducing risk and simplifying compliance efforts.
How StorageGuard works
Simple. No agents.
1. Deploy the StorageGuard software on a designated virtual machine and onboard your storage and backup systems. 2. Add specific checks to your baseline or just select all.
3. Run a scheduled or on-demand analysis and view findings within minutes.
Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.