Don’t Rely On Immutable Backup For Protection Against Ransomware
About Continuity™
StorageGuard - by Continuity™ - is the ONLY Security Posture Management solution for Storage & Backups, helping to ensure these systems are securely configured, and compliant with industry & security standards.
Introduction
“93% of cyberattacks target backups to force ransom payment” – this was the shocking headline from Veeam’s 2023 Ransomware Trends Report, which claimed that out of this number, cybercriminals succeeded in penetrating backups in 75% of cases and in 39% of cases, backup repositories were completely lost.
Since backups are becoming lucrative targets for cybercriminals, vendors like Cohesity, Commvault, Dell, Rubrik, Veeam and Veritas NetBackup have responded with new ransomware protection features. These include:
Immutable Backup
Once backed-up, the data is fixed and unchangeable. It can never be deleted. Organizations gain an always-recoverable and secure backup despite unforeseen events such as ransomware.
Immutability is an important capability; however, it can lead to a false sense of security if not implemented properly. When misconfigured, it is possible to delete supposedly immutable data, for example, by manipulating time/date settings on the storage device to bypass retention enforcement mechanisms.
One of the best practices by the backup vendors is to ensure immutable backups are configured with retention lock – a parameter that prevents their deletion for a minimum period of time – even if the backup pools the store them fill up. If retention lock is not configured, cybercriminals can attack backup by modifying large amounts of data, thereby quickly filling up the backup pools which results in deletion of all existing backups to free up space.
Even when retention lock is enabled, care must be taken to make sure cybercriminals can’t fool the backup systems to believe time is passing more quickly than intended (“time zapping” attacks – where the attacker manipulates insufficiently secure time sync configuration to trick the backup systems into thinking that “X” years have passed).
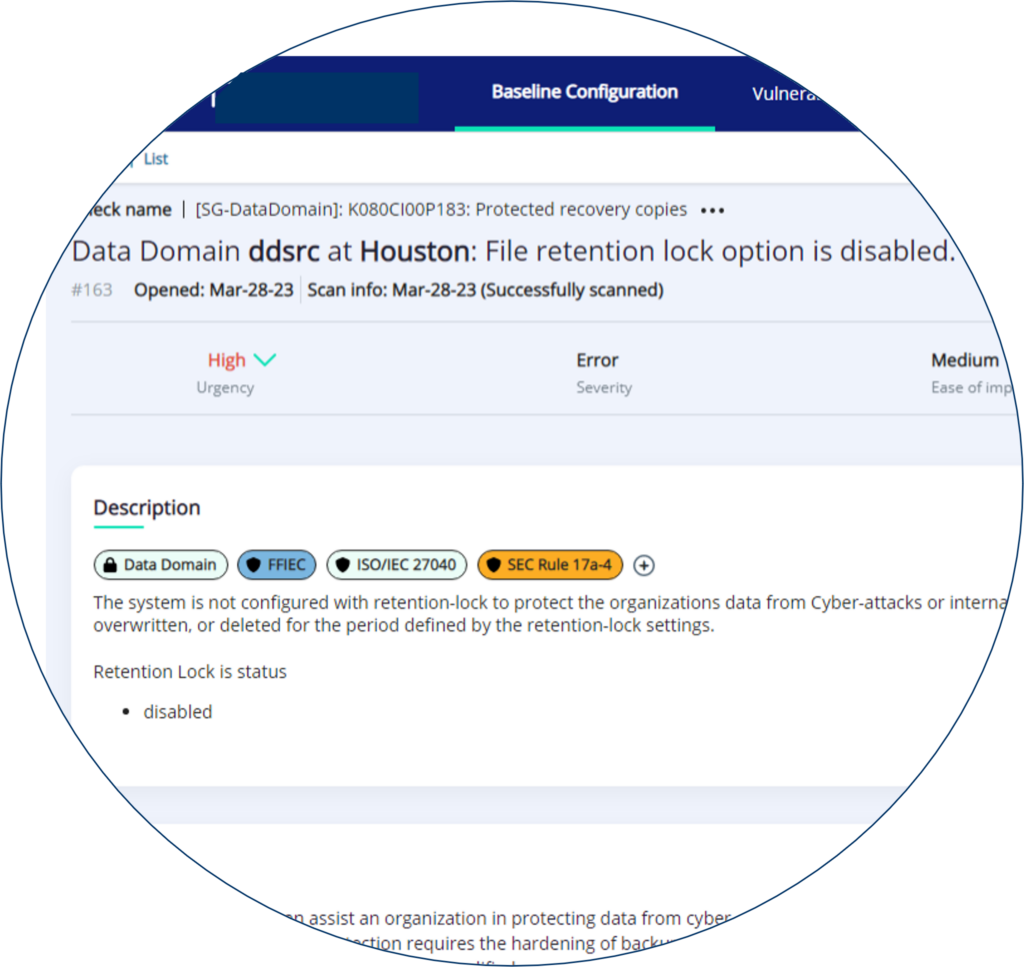
Source: Example of StorageGuard detecting a retention lock misconfiguration in Dell PowerProtect DD
Another threat is data poisoning. If cybercriminals can access backup systems, they can tamper with backup jobs, poison data before it is immutably backed-up, and render it useless when it comes to recovery. If they manage to keep the attack running unnoticed for sufficiently long time (say, several months), and then initiate a ransomware attack – organizations are left with no current backups to restore from.
But there are other errors that can contribute to backup challenges. Too many times, organizations don’t find time to test backups to ensure their systems are recoverable. It is also common for them to fail to log unauthorized entries into backup and storage systems. Thus, they don’t spot compromised backup jobs.
To make matters worse, some organizations purchase immutability features and then either don’t activate the necessary licenses, or don’t turn on the retention lock feature.
Snapshots & Replication
A complete storage hardware-level copy of the data is made at certain points of the day (snapshots) or the data at one location is replicated entirely to another location. Very often, such copies are not secured and isolated well enough. For example, a server admin role should not be allowed to manipulate storage copies – but many organizations fail to observe this best practice. This allows hackers that gain access to servers, to also delete their storage-based copies. If the data being snapshotted or replicated is corrupted, recovery won’t be possible.
Air-Gapped and Offline Copies
Air gapping ensures you retain a copy of the data in an environment that is completely inaccessible from your network (and from the Internet, for that matter), or offline (i.e., not connected to your endpoints, or completely powered off).
A time-tested way to do this is via tapes that are either physically removed from the network or sit offline in a safe. There are cloud and disk-based systems, too, that claim air-gap capabilities. However, such systems are almost never fully offline. There is always a danger that a misconfiguration, vulnerability or human error will expose the data to the network – or allow hackers to interfere with the data unnoticed
If There Are So Many Advanced Data Protection Tools, How Are Cybercriminals Still Succeeding?
A recent Enterprise Strategy Group survey found enterprises are making strides in ransomware preparedness, but work remains to prevent and mitigate attacks.
The survey asked how organizations currently tackle ransomware. Respondents said the most important prevention tactics involve efforts in network security (43%), followed closely by backup infrastructure security (40%).
When asked about the top ransomware issues that required the most attention, 43% said they felt very concerned about their backups suffering infection or corruption following a ransomware attack, and an additional 44% said they were somewhat concerned.
“Because it’s talked about so frequently, we think about the initial entry point coming from some phishing exercise. But the data showed the most common entry points for ransomware weren’t email threat factors, but rather software configuration vulnerabilities.”  Dave Gruber, Analyst at Enterprise Strategy Group (ESG) |
Even with all the new ransomware prevention features being developed by the backup and data protection vendors, it turns out that backup vulnerabilities, weak security settings, and misconfigurations are handing cybercriminals a relatively easy passage into organizations. From there, they can cripple backups, lock users out of systems, and hold organizations to ransom.
Similarly, security misconfigurations and vulnerabilities in production storage systems and archival locations for backups can be exploited by cybercriminals to gain access to production data and compromise the recovery plan.
And if that’s not enough, configuration drifts result in backup systems being non-compliant with the organization’s security baseline, vendor’s security guidelines and industry standards.
External Forces
The growing number of ransomware attacks targeting backups has led to new industry standards that require organizations to prove they meet ISO and NIST storage & backup guidelines, as well as increased compliance burden in response to growing backup threats and national standards, like the new DORA framework in Europe.
And if that’s not enough, insurance firms have dramatically raised the barrier for cyber coverage eligibility, which requires not only technological features, such as immutability – but also validation of the soundness of backup security controls, such as separation of administrative planes, patching, testing, etc.
Here’s an example of Chubb’s application form
Filling The Gap
StorageGuard verifies that your backup systems (from the likes of Cohesity, Commvault, Dell, Rubrik, Veeam and Veritas NetBackup) are hardened, configured according to industry and vendor security best practices, and are not vulnerable:
- Verifies that anti-ransomware features are enabled and configured correctly (e.g., ransomware detection, ransomware isolation, anomaly detection, user behavioral analysis, and AV scanning)
- Verifies that snapshots, replicas, images, and backup sets which are required for recovery from ransomware – are secure, immutable isolated and generally protected
- Verifies that ransomware protection best practices published by storage and backup vendors are implemented
- Validates that data volumes, exports and shares are configured with restricted access and privileges, and according to security best practices
- Allows you to choose the standard sets you wish to comply with, and automating compliance reporting, highlighting gaps, prioritizing risks, and facilitating automated remediation.
To summarize, StorageGuard plays a critical role in your cyber resiliency strategy, by helping you increase usage & adoption of your existing data protection tools – and subsequently get more out of your current investment.
“Bad actors can gain access to the backup system, change the configuration, and then delete the immutable backups. This is why its so important to run a ransomware assessment on storage and backups”  Jim Brady, CISO at Fairview Health Services |
Find out today how secure your immutable storage and backups are.
In just 2 minutes, receive a maturity score and practical recommendations, to help secure your backups, protect your data, and ensure recoverability.

https://www.esg-global.com/hubfs/ESG-Infographic-2022-Ransomware-Landscape.pdf
Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.