
After The Johnson Controls Ransomware Attack, Here’s An 8-Point Security Checklist For Your Backups
About Continuity™
StorageGuard - by Continuity™ - is the ONLY Security Posture Management solution for Storage & Backups, helping to ensure these systems are securely configured, and compliant with industry & security standards.
On September 27th, Johnson Controls International announced a massive ransomware attack, that encrypted many of the company devices, including VMware ESXi servers. This impacted the company’s and its subsidiaries’ operations.
The company serves clients in the government, healthcare, and naval sectors, and they believe sensitive Department of Homeland Security (DHS) information may have been compromised in this attack.
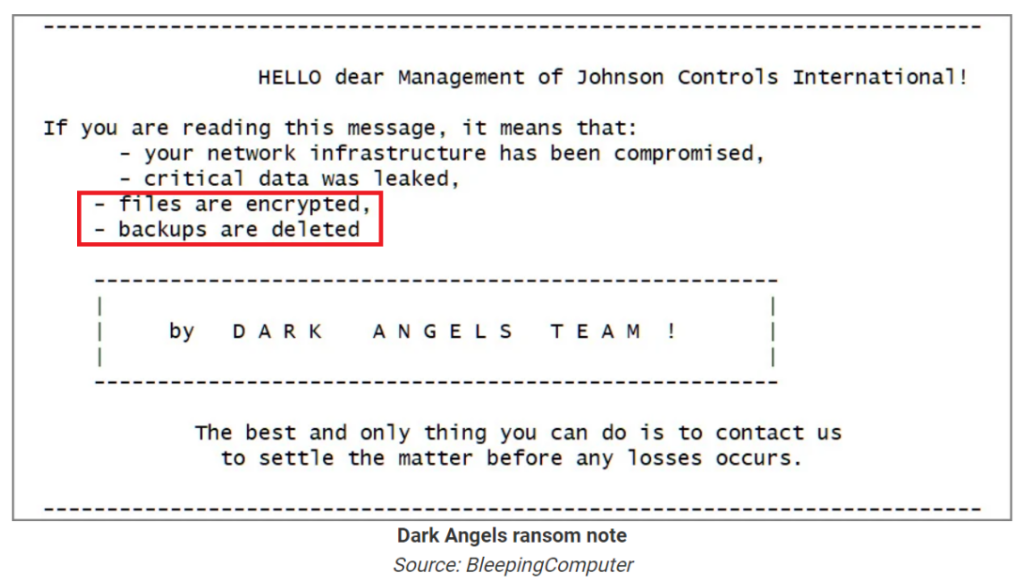
What was unique about this incident, was the ransom note sent by Dark Angels, the ransomware group, which included the following details: “Files are encrypted. Backups are deleted”. While this isn’t the first time ransomware groups have successfully breached their victim’s backup environments (See recent News Headlines: https://www.continuitysoftware.com/resources/?resources_category=headlines), it is one of most publicized attacks.
Your 8-Point Checklist To Secure Your Backups
A ransomware attack is a horrible time to discover that your backups are not secure, so to help, here’s an 8-point checklist to determine whether your backups are sufficiently secured, and whether data is fully protected.
- Do your security incident-response plans include cyberattacks on your backups? If so, what’s included:
- Recovery from a complete wipe of a storage array
- Recovery from a complete corruption of the SAN fabric configuration
- Recovery from ransomware
- Is there a complete inventory of your storage and backup devices, that includes the current security status for each one?
- All backups, archive environments, storage arrays (block, file, object), and SAN switches
- Storage software versions (storage OS, firmware deployed), and, in particular: patching status, known CVEs, and actual resolution status
- What is backed up? Where? How?
- Which storage & backup protocols are allowed? Are all obsolete and insecure protocols disabled
- Is there comprehensive and secure event logging and auditing of your backups?
- Including: central log services, redundant and tamper-proof records, and redundant and reliable time service
- Are you able to audit the configuration changes?
- e.g., what changed and when – in device configuration, storage mapping, and access control?
- Is there a well-documented, and enforced separation of duties for your backups?
- e.g., separate admins for storage, backup, and disaster recover in each environment
- Are all storage and backup administrative-access mechanisms documented?
- e.g., which APIs are open, how many central storage management systems can control each storage device, and are there any servers or OS instances that can control storage
- Are existing mechanisms for ransomware protection, air-gapping, and copy-locking used?
- Is there an audit process to verify they are correctly deployed at all times?
- Is the security of your backups regularly audited?
- Does this audit process include: SAN communication devices, storage arrays (block, file, object), server-based SAN, and backup?
Take the 2-minute Ransomware Resiliency Assessment for Backups, and get your own maturity score and practical recommendations – to help protect your data, and ensure recoverability.
Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.