Configuration Compliance for Storage & Backups
Check the Security of Your Storage & Backups
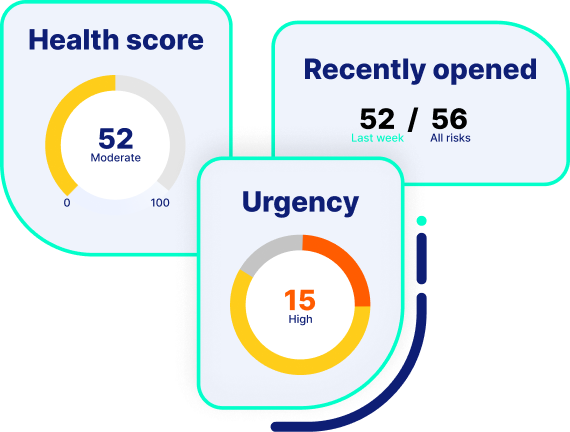
StorageGuard is the ONLY solution that analyzes the security configuration of your storage & backup systems – to ensure they’re secure, and compliant with regulations. How secure are your storage & backups?
Respected Brands Trust Continuity™
StorageGuard
The ONLY Security Posture Management solution that securely configures all enterprise storage & backup systems, ensuring data remains secure.
StorageGuard scans, detects, and fixes security misconfigurations and vulnerabilities across hundreds of storage, backup and data protection systems – including Dell, NetApp, Hitachi Vantara, Pure, Rubrik, Commvault, Veritas, HPE, Brocade, Cisco, Veeam, Cohesity, IBM, Infinidat, VMware, AWS and Azure.
- Baseline. Establish a security baseline for your storage & backups
- Configure. Detect deviation from a chosen Configuration Baseline, and securely configure your storage & backup systems
- Detect. Detect when industry & vendor configuration best practices aren’t implemented, and validate adherence to ransomware protection guidelines
- Compliance. Automatically prove audit compliance for your storage & backups (e.g., CIS Controls, NIST, ISO, PCI, NERC CIP, etc.)
- Fix. Quickly detect and remediate vulnerabilities & security misconfigurations in your storage & backups
On September 27th, Johnson Controls Suffered A Massive Ransomware Attack, Which Included Deleted Backups


What’s our secret sauce?
- We are the ONLY company that securely hardens all storage & backup systems – from every vendor, by detecting vulnerabilities & security misconfigurations.
- We have built the most comprehensive Knowledge Base of security risks & best practices for enterprise storage & backup environments.
CISOs Guide To ISO 27040: Storage Security
The release of ISO/IEC 27040:2024 provides an overview, analysis, and guidance for the security of storage & backup systems.

Talk To An Expert
It’s time to automate the secure configuration of your storage & backup systems.